What is NIST CSF?
 The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a set of guidelines designed to help organizations manage and mitigate cybersecurity risks. Originally released in 2014, the NIST CSF was developed in response to a Presidential Executive Order to enhance the security of the nation’s critical infrastructure. It has since become a widely adopted standard across various industries due to its flexibility, comprehensiveness, and alignment with other standards and best practices. The framework’s core was originally built around five high-level functions: Identify, Protect, Detect, Respond, and Recover, each addressing a crucial aspect of cybersecurity management.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a set of guidelines designed to help organizations manage and mitigate cybersecurity risks. Originally released in 2014, the NIST CSF was developed in response to a Presidential Executive Order to enhance the security of the nation’s critical infrastructure. It has since become a widely adopted standard across various industries due to its flexibility, comprehensiveness, and alignment with other standards and best practices. The framework’s core was originally built around five high-level functions: Identify, Protect, Detect, Respond, and Recover, each addressing a crucial aspect of cybersecurity management.
Why NIST CSF is a Valuable Standard
NIST CSF 2.0: Recent Updates
In response to evolving cybersecurity challenges and community feedback, NIST recently released an updated version of the framework, known as NIST CSF 2.0. This version incorporates several significant enhancements:
1. Governance Function: The addition of a sixth core function, Govern, highlights the importance of cybersecurity governance in risk management.
2. Improved Implementation Guidance: Provides more practical steps and detailed guidance for organizations at different stages of cybersecurity maturity.
3. Supply Chain Risk Management: Emphasizes the critical role of managing risks associated with third-party relationships.
4. Integration with Other NIST Guidelines: Promotes the ability to leverage other NIST publications, such as the Risk Management Framework (RMF) and the Privacy Framework.
5. International Alignment: Better aligns with international cybersecurity standards and practices.
Understanding and Progressing Through the Tiers
A key component of NIST CSF 2.0 is the revised tier system, which describes the maturity of an organization’s cybersecurity risk management practices. This system ranges from Tier 1 (Partial) to Tier 4 (Adaptive), each representing a higher level of sophistication and integration. Each of these tiers is an overarching description of where your organization sits in terms of risk management processes and how thoroughly integrated risk management is with the company culture.
For organizations looking to enhance their cybersecurity posture, the journey typically begins at Tier 1 and progresses through the higher tiers as they develop more robust and systematic risk management practices.
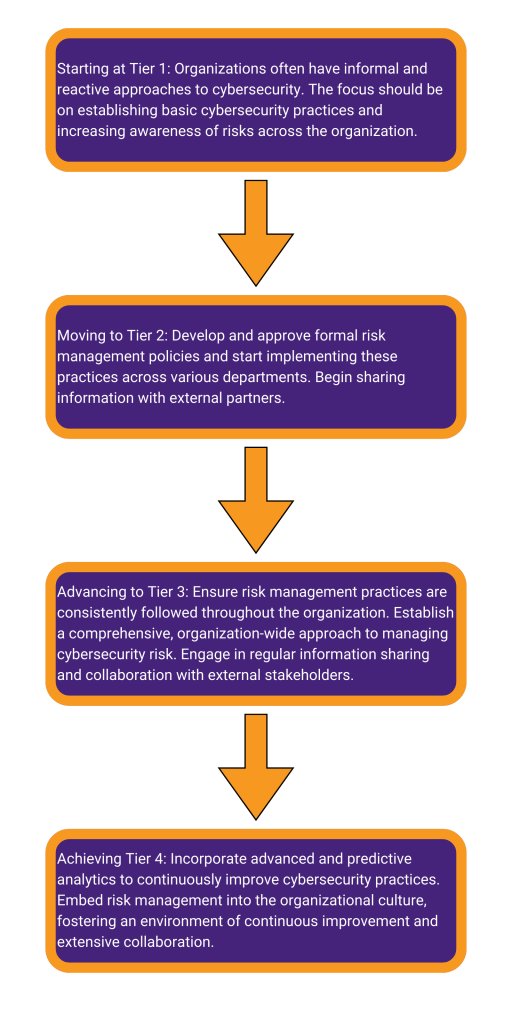
By following this structured progression, organizations can systematically enhance their cybersecurity capabilities, ultimately leading to a more resilient and secure environment.
NIST CSF 2.0 represents a significant step forward in cybersecurity risk management, offering organizations a detailed and flexible framework to guide their cybersecurity efforts. By understanding and implementing the updated tier system, organizations can effectively measure and improve their cybersecurity maturity over time.
If NIST seems like the type of standard that you would like to hold your own company to but aren’t sure where to even begin to get to a tier 1 level, BizCom is here to help you. We have experts who know the ins and out of every NIST CSF control and will help guide you to a safe and secure environment.




